Search for person "David Hebbeker" returned 140 results
47 min
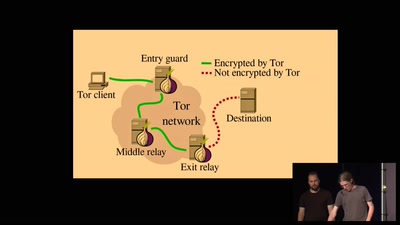
Introduction to Mix Networks and Katzenpost
a new anonymity movement

55 min
Container-Orchestrierung in der Cloud für Profis
Cluster-Treiber anpassen in OpenStack Magnum

13 min
Wie moderne Technologien unsere Gesellschaft nachhaltiger gestalten können.
Können wir mit Hilfe künstlicher Intelligenzen den…

34 min
Little Services, Big Risks
Extending capability-based security models to achieve…

22 min
What's new in OBS?
Latest new features and how to use them
23 min