Search for person "Peter van Eijk" returned 267 results
61 min
25 Jahre Chipkarten-Angriffe
Von der Historie zur Zukunft

31 min
The DRM Of Pacman
Copy protection schemes of way back then and how they…

71 min
30C3 Infrastructure Review
Presentation of MOC/NOC/VOC/SOC/*OC

57 min
29C3 GSM: Cell phone network review
262 42 - The full spectrum

58 min
Setting mobile phones free
An overview of a mobile telephony market and how a…

55 min
Our daily job: hacking the law
The key elements of policy hacking

38 min
Der Inhalt dieses Vortrags ist in deinem Land leider nicht verfügbar.
oder wie man in einen Walfisch klettert, ohne ihn dabei zu…
64 min
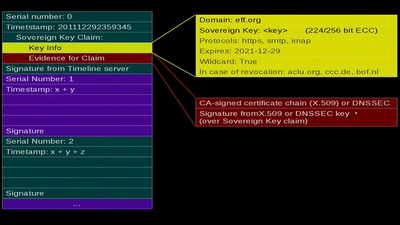
Sovereign Keys
A proposal for fixing attacks on CAs and DNSSEC
51 min
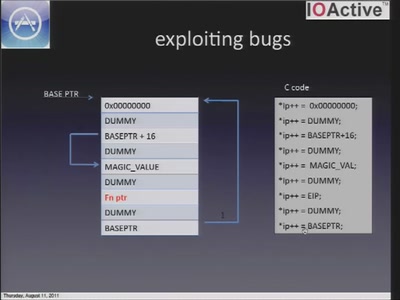
iOS application security
A look at the security of 3rd party iOS applications
56 min
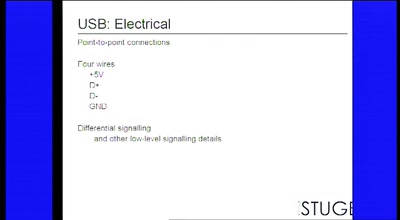
USB and libusb
So much more than a serial port with power
60 min
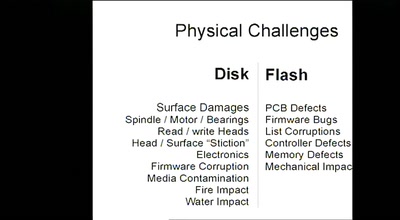
Data Recovery Techniques
Fun with Hard Drives
73 min
hacking smart phones
expanding the attack surface and then some

58 min
Is the SSLiverse a safe place?
An update on EFF's SSL Observatory project

70 min
coreboot: Adding support for a system near you
Working with the open source BIOS replacement and getting a…

78 min
Radio der Zukunft
Was kommt nach dem analogen Radio?

83 min
Software-Patente. Nicht schon wieder!
Es geht wieder los. Diesmal ist es aber vielleicht das…

50 min
coreboot: Beyond The Final Frontier
Open source BIOS replacement with a radical approach to…

44 min
Why technology sucks
If technology is the solution, politicians are the problem

63 min