Search for "Anna" returned 400 results

53 min
Cryptography demystified
An introduction without maths

53 min
Hacken Dicht
Die Aftershow-Party

62 min
Kyber and Post-Quantum Crypto
How does it work?
65 min
The exhaust emissions scandal („Dieselgate“)
Take a deep breath into pollution trickery
42 min
We do Privacy by Design
Best practices and real-life examples

32 min
The Case for Scale in Cyber Security
Security Track Keynote

37 min
Hacking (with) a TPM
Don't ask what you can do for TPMs, Ask what TPMs can do…
72 min
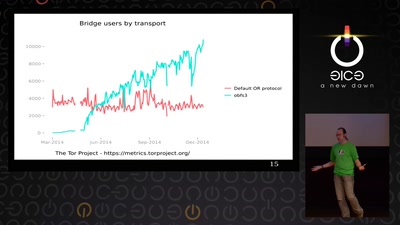
State of the Onion
Neuland

44 min
Exploiting PHP7 unserialize
teaching a new dog old tricks

58 min
PLC-Blaster
Ein Computerwurm für PLCs

60 min
the possibility of an army
phone verified accounts bringing the Hessian army back to…

61 min
About Gamma-Ray Bursts And Boats
What We (Don't) Know About the Most Energetic Events in the…

58 min
Uncertain Concern
How Undocumented Immigrants in the US Navigate Technology

60 min
Mein Bot, der Kombattant
Operative Kommunikation im digitalen Informationskrieg

60 min
Why is GPG "damn near unusable"?
An overview of usable security research
61 min
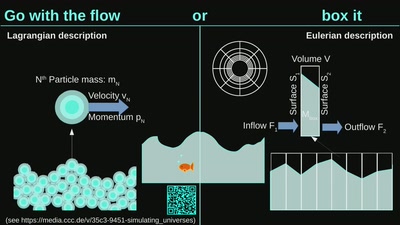
Grow your own planet
How simulations help us understand the Universe
31 min
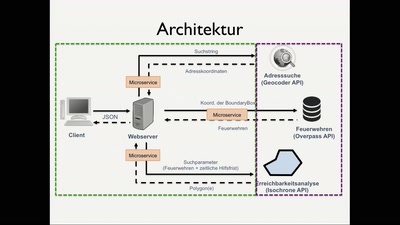
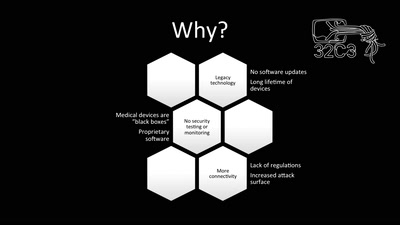
Lightning Talks II
DeepVGI - Einsatz von Lowcost-Lidarsystemen für die…
60 min