Search for "anna" returned 428 results

30 min
The Machine To Be Another
Exploring identity and empathy through neuroscience,…

50 min
Heimlich-Manöver
Best of Informationsfreiheit & Gefangenenbefreiung

53 min
Cryptography demystified
An introduction without maths

29 min
Es sind die kleinen Dinge im Leben II
was alles geht und wie man anfängt, mit Mikroskopen

44 min
Open Code Verlesung
Lesung des öffentlichen Sourcecodes

53 min
Hacken Dicht
Die Aftershow-Party

62 min
Kyber and Post-Quantum Crypto
How does it work?

55 min
Chatkontrolle
Ctrl+Alt+Delete
65 min
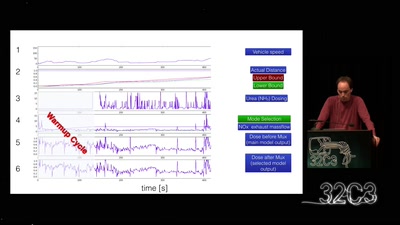
The exhaust emissions scandal („Dieselgate“)
Take a deep breath into pollution trickery
42 min
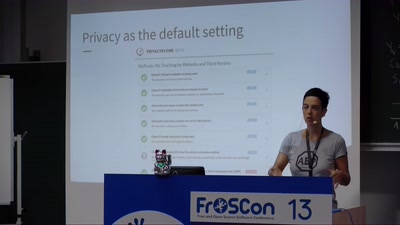
We do Privacy by Design
Best practices and real-life examples

37 min
Hacking (with) a TPM
Don't ask what you can do for TPMs, Ask what TPMs can do…

58 min
selbstverständlich antifaschistisch!
Aktuelle Informationen zu den Verfahren im Budapest-Komplex…

58 min