Search for "sECuRE" returned 791 results

33 min
Gone in 60 Milliseconds
Intrusion and Exfiltration in Server-less Architectures
60 min
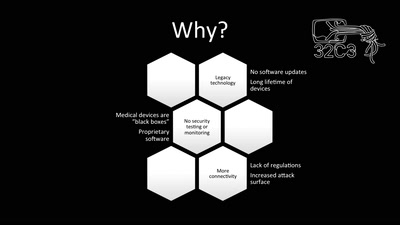
Unpatchable
Living with a vulnerable implanted device

55 min
Encrypted Email for Planet Earth
Failures, Challenges, and the Future
44 min
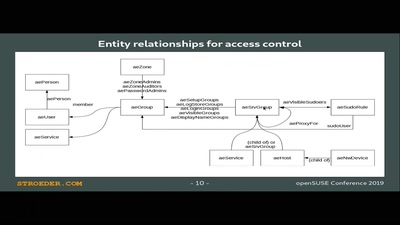
Æ-DIR -- Authorized Entitites Directory
Identity and Access Management with OpenLDAP

39 min
My Safe In Your House
Keeping Secrets On Remote Machines
35 min
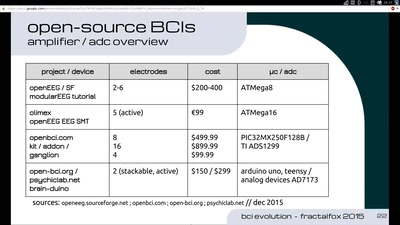
Evolution of Brain-Computer Interfaces
The future of Neuro-Headsets and concepts towards…

45 min
Machine-to-machine (M2M) security
When physical security depends on IT security

39 min