Search for "JO" returned 10055 results
47 min
Finding Vulnerabilities in Internet-Connected Devices
A Beginner’s Guide

48 min
The gift of sharing
A critical approach to the notion of gift economy within…

31 min
A Tale of Two Leaks:
How Hackers Breached the Great Firewall of China
61 min
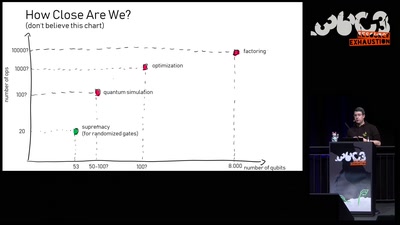
Quantum Computing: Are we there yet?
An introduction to quantum computing and a review of the…
40 min