Search for "Tii" returned 752 results
38 min
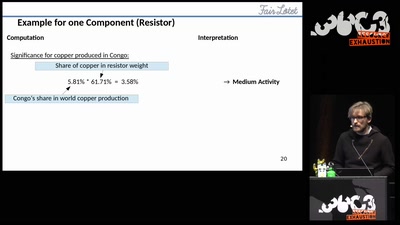
Fairtronics
A Tool for Analyzing the Fairness of Electronic Devices
43 min
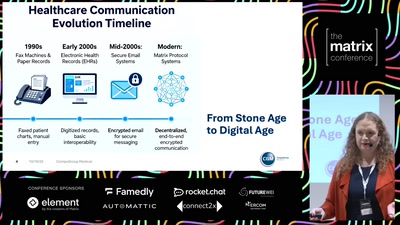
Matrix as a Bridge
Enabling Cross-Border Healthcare Communication Through Open…

44 min
What the cyberoptimists got wrong - and what to do about it
Tech unexeptionalism and the monopolization of every…

54 min
Swedish analysis of Nazi crypto TTYs
How Beurling et al. broke the Siemens & Halske T52 crypto…

32 min
The Case for Scale in Cyber Security
Security Track Keynote
41 min
A WebPage in Three Acts
live coding performance

63 min
All cops are broadcasting
TETRA unlocked after decades in the shadows

45 min
Triggering Deep Vulnerabilities Using Symbolic Execution
Deep program analysis without the headache

51 min
Reverse Engineering the MOS 6502 CPU
3510 transistors in 60 minutes
24 min
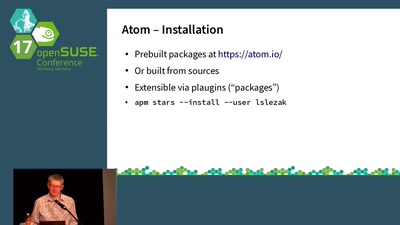
The Atom Editor
A Hackable Text Editor for the 21st Century
40 min
The Extremely Large Telescope (ELT)
Building the biggest optical telescope on earth

37 min