Search for "W. Heck" returned 1226 results
58 min
Operation Triangulation
What You Get When Attack iPhones of Researchers
47 min
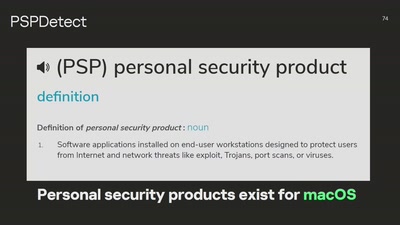
All cops are broadcasting
Obtaining the secret TETRA primitives after decades in the…
95 min
Hacker Jeopardy
Zahlenraten für Geeks
35 min
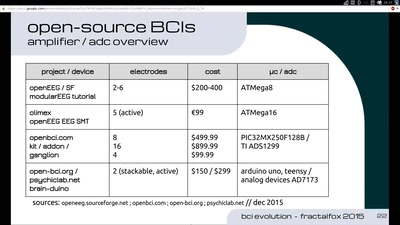
Evolution of Brain-Computer Interfaces
The future of Neuro-Headsets and concepts towards…

43 min
#NoPNR – Let’s kill the next Data Retention Law
How to Stop the Dubious Use of Passenger Name Records by…
46 min
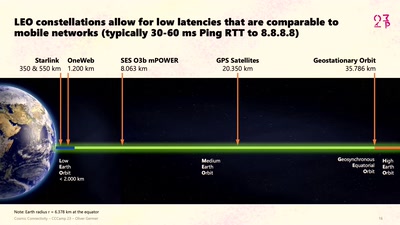
Cosmic Connectivity
Starlink, Satellite Swarms, and the Hackers' Final Frontier

47 min
Bug class genocide
Applying science to eliminate 100% of buffer overflows

103 min
Comparison of WAN IGP protocols
RSTP+flooding/learning for Ethernet, OSPFv2 for IPv4, and…

38 min
What your phone won’t tell you
Uncovering fake base stations on iOS devices
60 min
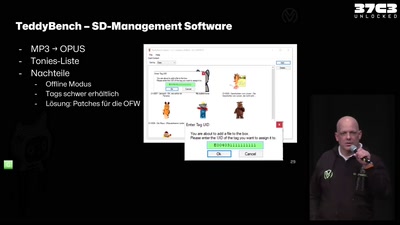
Toniebox Reverse Engineering
Eine Musikbox für Kinder, Maker und Hacker
71 min