Search for "csk" returned 1253 results

61 min
Safe and Secure Drivers in High-Level Languages
How to write PCIe drivers in Rust, go, C#, Swift, Haskell,…

44 min
Lützerath Lebt! Einblicke in den Widerstand
Für globale Klimagerechtigkeit kämpfen

58 min
Polizeigesetze
Endlich viele neue Gründe zu demonstrieren

61 min
Deploying TLS 1.3: the great, the good and the bad
Improving the encrypted the web, one round-trip at a time
65 min
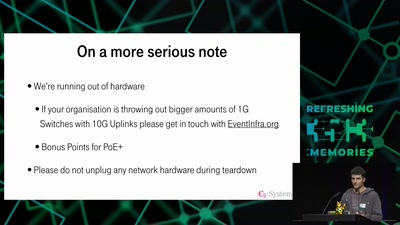
35C3 Infrastructure Review
Up and to the right: All the statistics about this event…
43 min
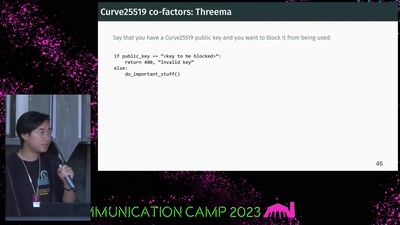
If It Ain't Broken, Do Fix It
Building Modern Cryptography
39 min
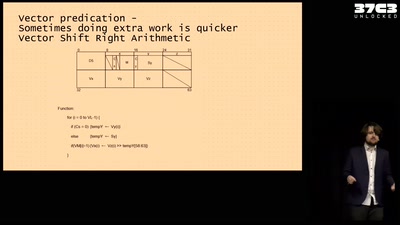
Making homebrew for your very own Vector Super Computer
Adventures running a NEC Vector Engine for fun and ...…

46 min
SELECT code_execution FROM * USING SQLite;
--Gaining code execution using a malicious SQLite database

36 min
Apple's iPhone 15: Under the C
Hardware hacking tooling for the new iPhone generation

49 min
BREACH in Agda
Security notions, proofs and attacks using dependently…

61 min