Search for "syb" returned 323 results

57 min
The Layman's Guide to Zero-Day Engineering
A demystification of the exploit development lifecycle

37 min
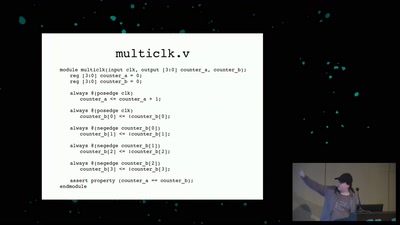
Hacking (with) a TPM
Don't ask what you can do for TPMs, Ask what TPMs can do…

60 min
Open Source is Insufficient to Solve Trust Problems in Hardware
How Betrusted Aims to Close the Hardware TOCTOU Gap

51 min
The GNU Name System
A Decentralized PKI For Social Movements
60 min
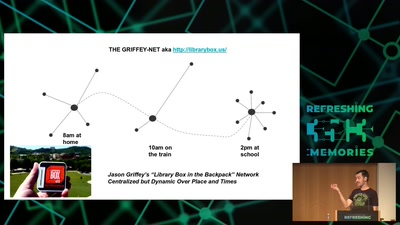
Wind: Off-Grid Services for Everyday People
Integrating nearby and offline connectivity with the…
55 min
SigOver + alpha
Signal overshadowing attack on LTE and its applications

47 min
Bug class genocide
Applying science to eliminate 100% of buffer overflows

57 min
How I Learned to Stop Reinventing and Love the Wheels
or having FUN with (home/hackerspace) robotics

55 min
White-Box Cryptography
Survey

58 min
Open Source Estrogen
From molecular colonization to molecular collaboration

49 min
Key-logger, Video, Mouse
How to turn your KVM into a raging key-logging monster

64 min
It Always Feels Like the Five Eyes Are Watching You
Five Eyes’ Quest For Security Has Given Us Widespread…

61 min
Now I sprinkle thee with crypto dust
Internet reengineering session

62 min
Kyber and Post-Quantum Crypto
How does it work?

60 min
On the insecure nature of turbine control systems in power generation
A security study of turbine control systems in power…
56 min