Search for "cy" returned 5947 results
39 min
The Eye on the Nile
Egypt's Civil Society Under Attack

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities
49 min
A short political history of acoustics
For whom, and to do what, the science of sound was…
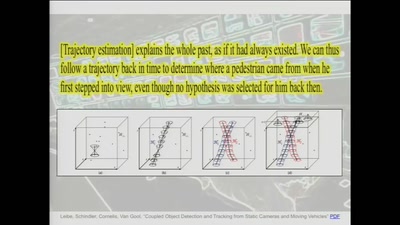
38 min
Policing the Romantic Crowd
Velocipedes and Face Recognition

50 min
Predictable RNG in the vulnerable Debian OpenSSL package
the What and the How
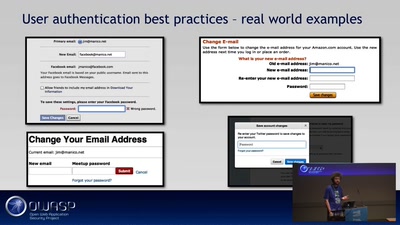
69 min
OWASP ProActive Controls
Sichere Anwendungen erstellen?
41 min