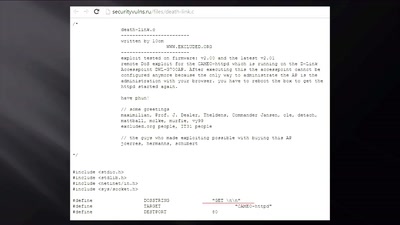
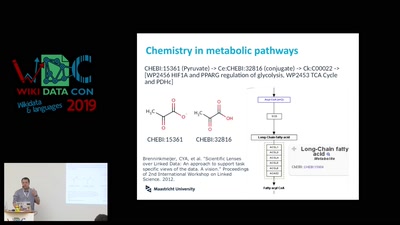
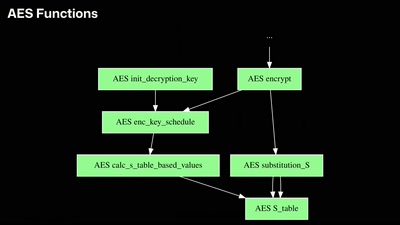
Search for "W. Heck" returned 1226 results
65 min
35C3 Infrastructure Review
Up and to the right: All the statistics about this event…
71 min
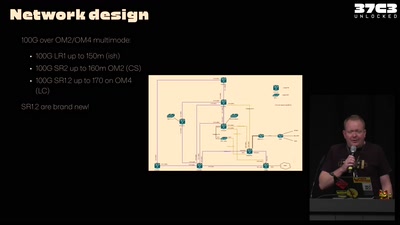
37C3 Infrastructure Review
Teams presenting how they helped making this awesome event

30 min
Science is broken
How much can we trust science in light failed replications,…
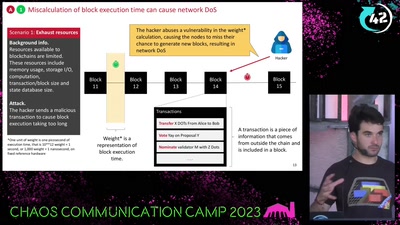
37 min
DON’T PANIC
bytes, blocks, bugs

46 min
Writing secure software
using my blog as example

60 min
Everything you always wanted to know about Certificate Transparency
(but were afraid to ask)
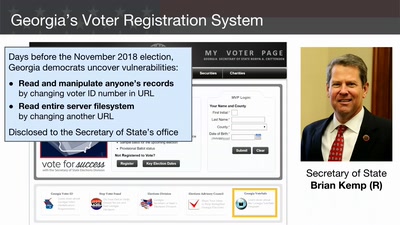
59 min
Election Cybersecurity Progress Report
Will the U.S. be ready for 2020?
41 min
Demoscene now and then
The demoscene is an underground computer art culture.

60 min
Beyond your cable modem
How not to do DOCSIS networks

40 min
The Great Escape of ESXi
Breaking Out of a Sandboxed Virtual Machine
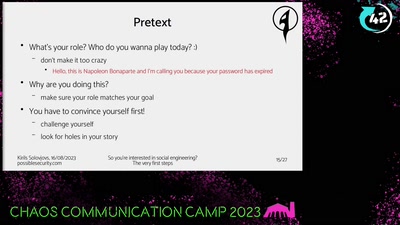
44 min
So you're interested in social engineering?
The very first steps
59 min
Towards General Purpose Reconfigurable Computing on Novena
FPGAs for Everybody with Novena

57 min
TrustZone-M(eh): Breaking ARMv8-M's security
Hardware attacks on the latest generation of ARM Cortex-M…

42 min
NEW IMPORTANT INSTRUCTIONS
Real-world exploits and mitigations in Large Language Model…

60 min
Lockpicking in the IoT
...or why adding BTLE to a device sometimes isn't smart at…

61 min
DevOps but for artworks in museums
A look into pipelines ending in museums and not in the cloud

43 min