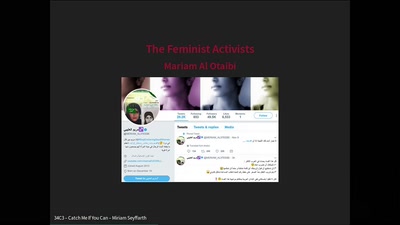
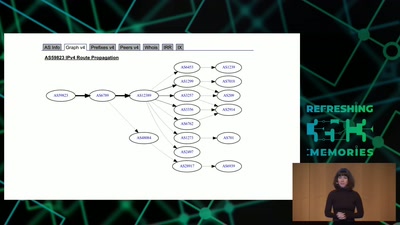
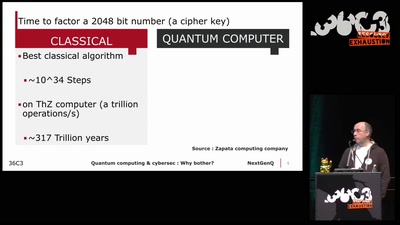
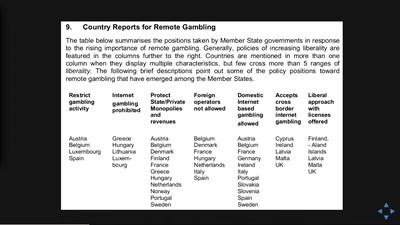
Search for "York University" returned 454 results

60 min
Why is GPG "damn near unusable"?
An overview of usable security research

60 min
Intel Management Engine deep dive
Understanding the ME at the OS and hardware level

26 min
Technomonopolies
How technology is used to subvert and circumvent…

42 min
Firmware Fat Camp
Embedded Security Using Binary Autotomy

57 min
Du kannst alles hacken – du darfst dich nur nicht erwischen lassen.
OpSec für Datenreisende
44 min
Replication Prohibited
3D printed key attacks

60 min
Free Software and Hardware bring National Sovereignty
Gaza as a case study

62 min
Corporate surveillance, digital tracking, big data & privacy
How thousands of companies are profiling, categorizing,…

60 min
A Story of Discrimination and Unfairness
Prejudice in Word Embeddings

58 min
07KINGSTON25 JAMAICA: MALARIA UPDATE Dispatches from Fort Meade
Reporting on the secret trial of Chelsea Manning

32 min
Technology and Mass Atrocity Prevention
Overview on Current Efforts - We Need Moar H4x0rs?!

49 min