Search for "kay" returned 3827 results

15 min
YaST: from the repository to the distributions
Continuous testing and delivery, the YaST way

60 min
Quantum Cryptography
from key distribution to position-based cryptography
60 min
„Nach bestem Wissen und Gewissen“ – Floskeln in der Politik
Politische Phrasologie – warum man aus dem ganzen Zeug, das…
29 min
Doing OpenBanking with FOSS
Openbanking in an open and fashionable way.

24 min
Getting the most of AutoYaST in 2022
Presenting some recent features you may have missed

29 min
Live: 20 Years FSFE
The long way for software freedom

33 min
UPSat - the first open source satellite
Going to space the libre way

49 min
SimpleVOC - Yet another Memcached?
Bausteine für eine Key/Value-Datenbank

27 min
Shine on R
Geospatial data processing the /Ahh/R way

62 min
The Price Of Dissent
The surveillance state & modern day COINTELPRO tactics
43 min
Contain yourselves
The Way We Build Systems is (Still) Wrong
59 min
Detangling remote interactions with neuroscience
How can you leverage neuroscience to enable higher quality…
32 min
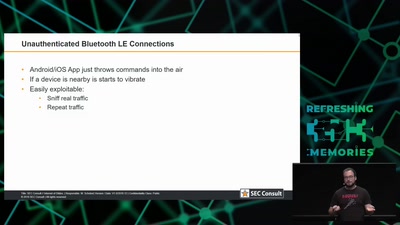
Internet of Dongs
A long way to a vibrant future
42 min
Cloud From Scratch
Building a small cloud the hard way
59 min
Millions of Lessons Learned on Electronic Napkins
On the way to free(ing) education

57 min
Cybercrime Convention
Hacking on its way to become a criminal act?

60 min
Ein Abgrund von Landesverrat
Wie es dazu kam und was daraus zu lernen ist

49 min
Lawful Interception in VoIP networks
Old Laws and New Technology the German Way
76 min
Linux - warum wechseln?
Wie ich zu Linux kam - und warum ich dabei bleibe
45 min