Search for "sECuRE" returned 791 results

58 min
Protecting Your Privacy at the Border
Traveling with Digital Devices in the Golden Age of…
62 min
The movements against state-controlled Internet in Turkey
A short account of its history and future challenges
59 min
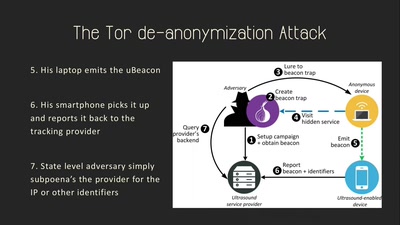
Talking Behind Your Back
On the Privacy & Security of the Ultrasound Tracking…

54 min
Sichere Softwareentwicklung
Ein praktischer Einstieg
59 min
Lernstick Linux als persönliche Lern- oder abgesicherte Prüfungsumgebung
für nachhaltige Geräteweiternutzung,…

51 min