Search for "Os Keyes" returned 602 results

28 min
Long war tactics
or how we learned to stop worrying and love the NSA

49 min
BREACH in Agda
Security notions, proofs and attacks using dependently…
60 min
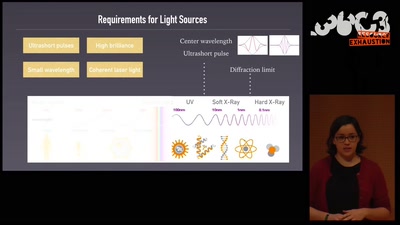
An ultrashort history of ultrafast imaging
Featuring the shortest movies and the largest lasers

45 min
Tech(no)fixes beware!
Spotting (digital) tech fictions as replacement for social…

49 min
Toward a Cognitive "Quantified Self"
Activity Recognition for the Mind

58 min
Thwarting Evil Maid Attacks
Physically Unclonable Functions for Hardware Tamper…

55 min
The Gospel of IRMA
Attribute Based Credentials in Practice

49 min
Dissecting VoLTE
Exploiting Free Data Channels and Security Problems
59 min
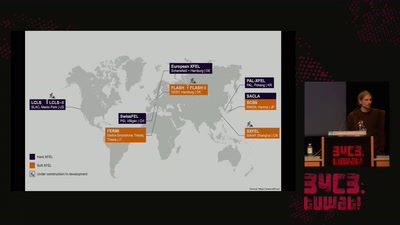
Free Electron Lasers
...or why we need 17 billion Volts to make a picture.

38 min
Afroroutes: Africa Elsewhere
VR experience "Beyond Slavery"
49 min
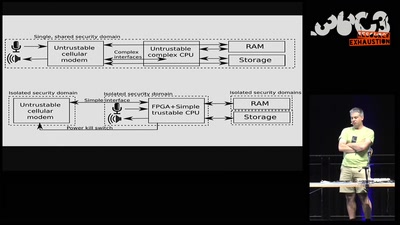
Creating Resilient and Sustainable Mobile Phones
Be prepared for the coming Digital Winter. And play…
39 min
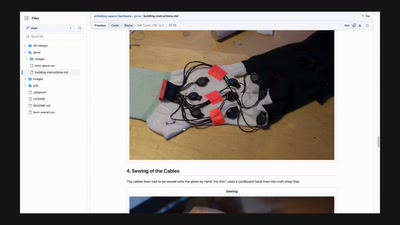
The Unfolding Space Glove
A Wearable for the Visually Impaired Translating 3D Vision…

58 min
When hardware must „just work“
An inside look at x86 CPU design

58 min
CIA vs. Wikileaks
Intimiditation surveillance and other tactics observed and…

64 min
Cory Doctorow – Fireside Chat
Reading and Q&A

48 min
Seidenstraße
The Making of…

42 min