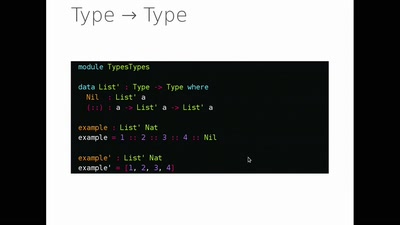
Search for "cbass" returned 381 results

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

61 min
Ten years after ‚We Lost The War‘
The future does not look much brighter than ten years ago.…
62 min
The Ghost in the Machine
An Artificial Intelligence Perspective on the Soul
65 min
35C3 Infrastructure Review
Up and to the right: All the statistics about this event…

53 min
No Love for the US Gov.
Why Lauri Love’s case is even more important than you…

53 min
Million Dollar Dissidents and the Rest of Us
Uncovering Nation-State Mobile Espionage in the Wild

56 min
WarGames in memory
what is the winning move?

55 min
How to Build a Mind
Artificial Intelligence Reloaded

77 min
Feminist Perspectives
Inclusive and Diverse Spaces and Communities

61 min
How Alice and Bob meet if they don't like onions
Survey of Network Anonymisation Techniques
46 min
Making machines that make
rapid prototyping of digital fabrication and…

51 min