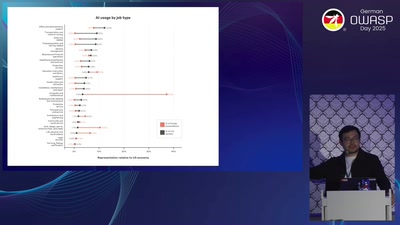
Search for "M" returned 11762 results

38 min
Endlich maschinenlesbare Urteile!
Open Access für Juristen
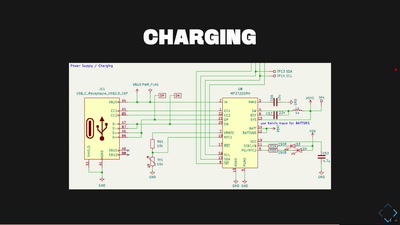
34 min
FeTAp 611 unplugged
Taking a rotary dial phone to the mobile age

39 min
Neuroexploitation by Design
Wie Algorithmen in Glücksspielprodukten sich Wirkweisen des…
42 min
Zentrum für Politische Schönheit:
Ein Jahr Adenauer SRP+ und der Walter Lübcke Memorial Park

39 min
Brennende Wälder und Kommentarspalten
Klimaupdate mit dem FragDenStaat Climate Helpdesk

31 min