Search for "Math" returned 1296 results

41 min
Chaos Communication Chemistry
DNA security systems based on molecular randomness

13 min
c3 MorningShow
Tag 2

36 min
Apple's iPhone 15: Under the C
Hardware hacking tooling for the new iPhone generation
40 min
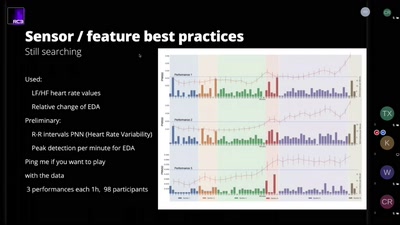
Boiling Mind
Analysing the link between audience physiology and…

31 min
Extended DNA Analysis
Political pressure for DNA-based facial composites

60 min
osmo-gmr: What's up with sat-phones ?
Piecing together the missing bits
38 min
A deep dive into the world of DOS viruses
Explaining in detail just how those little COM files…

55 min
ZombieLoad Attack
Leaking Your Recent Memory Operations on Intel CPUs

95 min