Search for "sECuRE" returned 792 results

64 min
It Always Feels Like the Five Eyes Are Watching You
Five Eyes’ Quest For Security Has Given Us Widespread…

58 min
Decoding Contactless (Card) Payments
An Exploration of NFC Transactions and Explanation How…

62 min
Kyber and Post-Quantum Crypto
How does it work?

56 min
Semestertickets ohne Überwachung
How I reverse engineered your public transport app

60 min
Sneaking In Network Security
Enforcing strong network segmentation, without anyone…
61 min
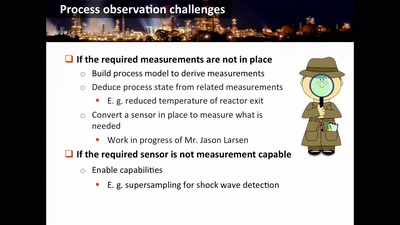
Damn Vulnerable Chemical Process
Exploitation in a new media
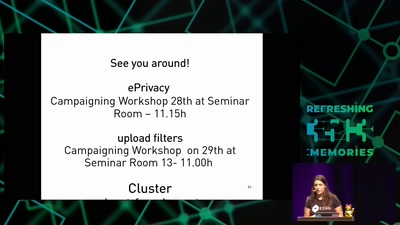
42 min
Citzens or subjects? The battle to control our bodies, speech and communications
A call to action to defend our ePrivacy and eliminate…

41 min