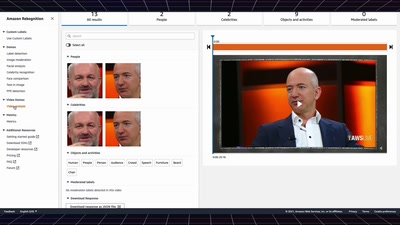
Search for "Elke Steven" returned 492 results

61 min
Trustworthy secure modular operating system engineering
fun(ctional) operating system and security protocol…

39 min
Web-based Cryptojacking in the Wild
When your browser is mining coins for other people
29 min
Heartache and Heartbleed: The insider’s perspective on the aftermath of Heartbleed
The untold story of what really happened, how it was…

113 min
Methodisch inkorrekt!
Die Wissenschaftsgala vom 33C3

55 min
Attribution revolution
Turning copyright upside-down with metadata
56 min
Rock' em Graphic Cards
Introduction to Heterogeneous Parallel Programming

61 min
Safe and Secure Drivers in High-Level Languages
How to write PCIe drivers in Rust, go, C#, Swift, Haskell,…

58 min
CIA vs. Wikileaks
Intimiditation surveillance and other tactics observed and…

56 min
Planes and Ships and Saving Lives
How soft and hardware can play a key role in saving lives…

61 min
How Alice and Bob meet if they don't like onions
Survey of Network Anonymisation Techniques
65 min
The exhaust emissions scandal („Dieselgate“)
Take a deep breath into pollution trickery
56 min
Deconstructing a Socialist Lawnmower
Obsolete Technologies + Critical Material Studies in Media…
50 min
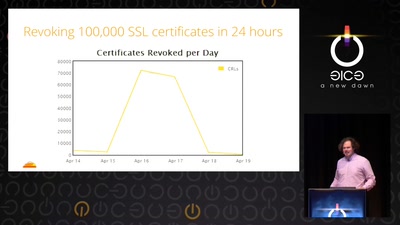
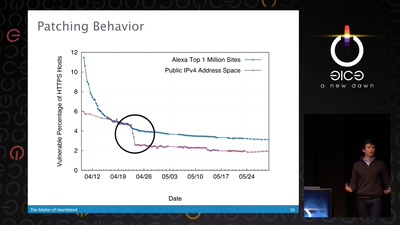
The Matter of Heartbleed
What went wrong, how the Internet reacted, what we can…

61 min
Now I sprinkle thee with crypto dust
Internet reengineering session

58 min
The Magic World of Searchable Symmetric Encryption
A brief introduction to search over encrypted data

63 min
The Global Assassination Grid
The Infrastructure and People behind Drone Killings

64 min