Search for "Eva" returned 481 results

26 min
Technomonopolies
How technology is used to subvert and circumvent…
71 min
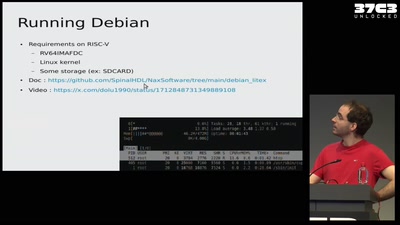
37C3 Infrastructure Review
Teams presenting how they helped making this awesome event
58 min
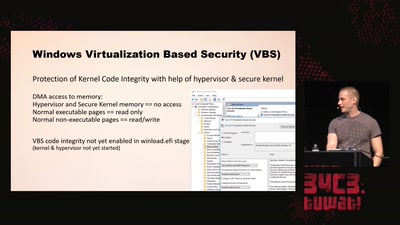
Operation Triangulation
What You Get When Attack iPhones of Researchers

61 min
About Gamma-Ray Bursts And Boats
What We (Don't) Know About the Most Energetic Events in the…
55 min
SigOver + alpha
Signal overshadowing attack on LTE and its applications

30 min
Syrian Archive
Preserving documentation of human rights violations

58 min
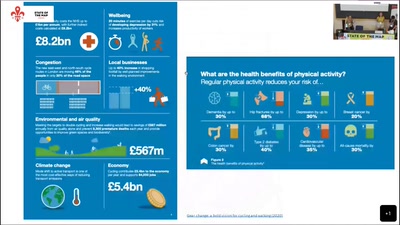
How risky is the software you use?
CITL: Quantitative, Comparable Software Risk Reporting

63 min
Reconstructing narratives
transparency in the service of justice

63 min
Das nützlich-unbedenklich Spektrum
Können wir Software bauen, die nützlich /und/ unbedenklich…

64 min
Decoding the LoRa PHY
Dissecting a Modern Wireless Network for the Internet of…
39 min
The Eye on the Nile
Egypt's Civil Society Under Attack

56 min
eMMC hacking, or: how I fixed long-dead Galaxy S3 phones
A journey on how to fix broken proprietary hardware by…
33 min
The Transhumanist Paradox
Deciding between technological utopias in a liberal state

58 min