Search for "sECuRE" returned 792 results

60 min
Attacking end-to-end email encryption
Efail, other attacks and lessons learned.
49 min
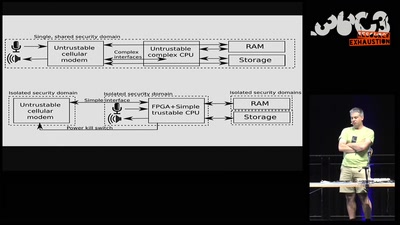
Creating Resilient and Sustainable Mobile Phones
Be prepared for the coming Digital Winter. And play…
46 min
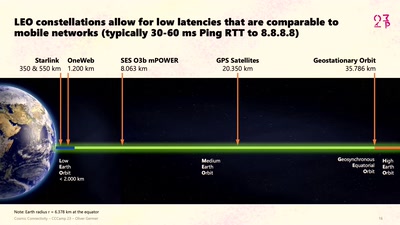
Cosmic Connectivity
Starlink, Satellite Swarms, and the Hackers' Final Frontier

41 min
Build a Fake Phone, Find Real Bugs
Qualcomm GPU Emulation and Fuzzing with LibAFL QEMU
10 min
Premiere: We love surveillance
#7reasons

55 min
Vehicle immobilization revisited
Uncovering and assessing a second authentication mechanism…
32 min
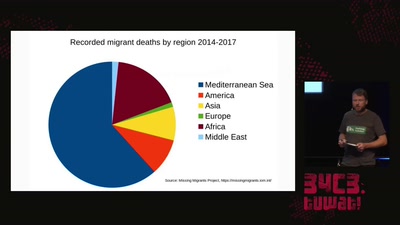
The seizure of the Iuventa
How search and rescue in the mediterranean was criminalized
43 min
WTF DJI, UAV CTF?!
A hacker's view at commercial drone security
47 min
All cops are broadcasting
Obtaining the secret TETRA primitives after decades in the…
60 min
The Perl Jam 2
The Camel Strikes Back
39 min
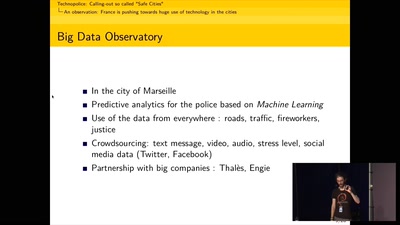
Technopolice: calling out so-called "Safe Cities"
Decentralising the fight against automated surveillance in…
45 min