Search for "max" returned 4568 results

55 min
Revisiting SSL/TLS Implementations
New Bleichenbacher Side Channels and Attacks

55 min
The Gospel of IRMA
Attribute Based Credentials in Practice
41 min
Framing digital industry into planetary limits and transition policies
The environmental costs of digital industry and pathways to…

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities
32 min
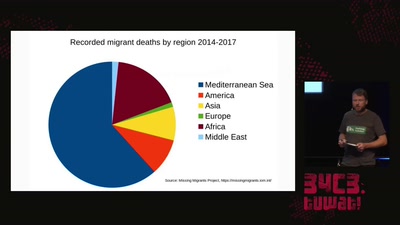
The seizure of the Iuventa
How search and rescue in the mediterranean was criminalized

53 min
Surveilling the surveillers
About military RF communication surveillance and other…

58 min
07KINGSTON25 JAMAICA: MALARIA UPDATE Dispatches from Fort Meade
Reporting on the secret trial of Chelsea Manning

41 min
Locked up science
Tearing down paywalls in scholarly communication
60 min
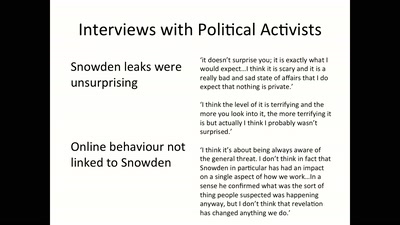
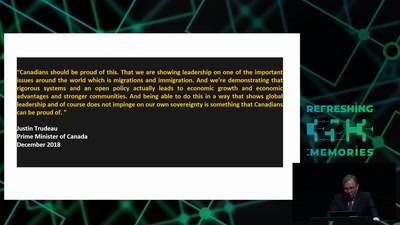
Media Coverage and the Public in the Surveillance Society
Findings from a Research Project on Digital Surveillance…
59 min