Search for "Max" returned 4566 results

60 min
the possibility of an army
phone verified accounts bringing the Hessian army back to…

41 min
Extracting keys from FPGAs, OTP Tokens and Door Locks
Side-Channel (and other) Attacks in Practice

60 min
Free Software and Hardware bring National Sovereignty
Gaza as a case study

61 min
Copywrongs 2.0
We must prevent EU copyright reform from breaking the…

58 min
Thwarting Evil Maid Attacks
Physically Unclonable Functions for Hardware Tamper…
33 min
Computer Science in the DPRK
A view into technology on the other side of the world

33 min
Interplanetary Colonization
the state at the beginning of the 21st Century

61 min
How Many Planets in Our Solar System? Glad You Asked!
How Astronomy Knew 6 Planets, Then Found 20 More, Then Went…
35 min
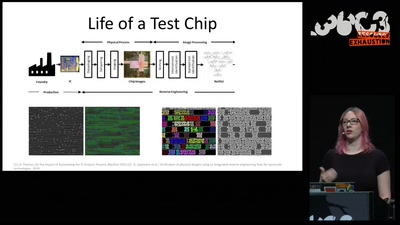
Understanding millions of gates
Introduction to IC reverse engineering for…

60 min
APT Reports and OPSEC Evolution, or: These are not the APT reports you are looking for
How advanced threat actors learn and change with innovation…

25 min
Regulating Autonomous Weapons
The time travelling android isn’t even our biggest problem

54 min