Search for "Eva" returned 481 results

60 min
Open Source is Insufficient to Solve Trust Problems in Hardware
How Betrusted Aims to Close the Hardware TOCTOU Gap

59 min
Visiting The Bear Den
A Journey in the Land of (Cyber-)Espionage

51 min
The GNU Name System
A Decentralized PKI For Social Movements

95 min
The Time is Right
Ein Science-Fiction-Theaterstück

55 min
Revisiting SSL/TLS Implementations
New Bleichenbacher Side Channels and Attacks
55 min
SigOver + alpha
Signal overshadowing attack on LTE and its applications

58 min
How risky is the software you use?
CITL: Quantitative, Comparable Software Risk Reporting

63 min
Das nützlich-unbedenklich Spektrum
Können wir Software bauen, die nützlich /und/ unbedenklich…

64 min
Decoding the LoRa PHY
Dissecting a Modern Wireless Network for the Internet of…
50 min
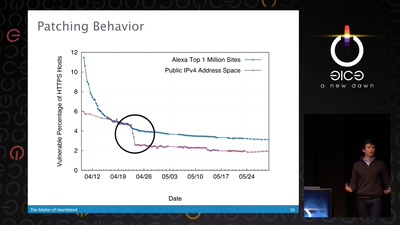
The Matter of Heartbleed
What went wrong, how the Internet reacted, what we can…

44 min
Exploiting PHP7 unserialize
teaching a new dog old tricks
43 min
WTF DJI, UAV CTF?!
A hacker's view at commercial drone security

58 min
The Magic World of Searchable Symmetric Encryption
A brief introduction to search over encrypted data

50 min
Connected Mobility hacken: digital.bike.23
Von E-Bikes in der Connected Mobility zur Entstehung eines…
67 min
Mit Kunst die Gesellschaft hacken
Das Zentrum für politische Schönheit

58 min