Search for "York University" returned 454 results

36 min
A Blockchain Picture Book
Blockchain origins and related buzzwords, described in…
62 min
A hacker's guide to Climate Change - What do we know and how do we know it?
An introduction to the basics of climate research and what…
62 min
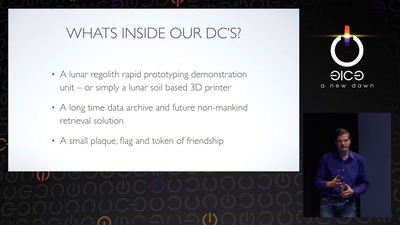
Space Hacker
Uploading rover...

63 min
A look into the Mobile Messaging Black Box
A gentle introduction to mobile messaging and subsequent…
62 min
The Ghost in the Machine
An Artificial Intelligence Perspective on the Soul

39 min
Web-based Cryptojacking in the Wild
When your browser is mining coins for other people

41 min
MicroPython – Python for Microcontrollers
How high-level scripting languages make your hardware…
64 min
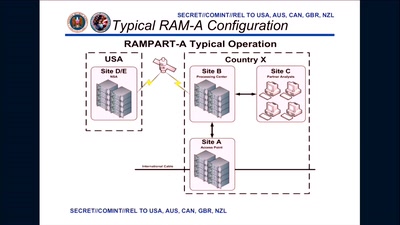
3 Years After Snowden: Is Germany fighting State Surveillance?
A Closer Look at the Political Reactions to Mass…
60 min
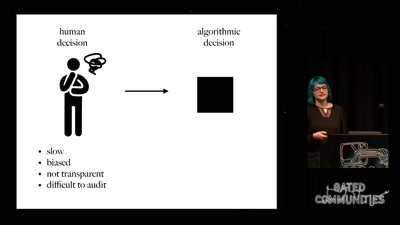
Prediction and Control
Watching Algorithms
62 min
Public Library/Memory of the World
Access to knowledge for every member of society
43 min
No PoC? No Fix! - A sad Story about Bluetooth Security
It is just a broken memcpy in the Bluetooth stack. Do we…

61 min
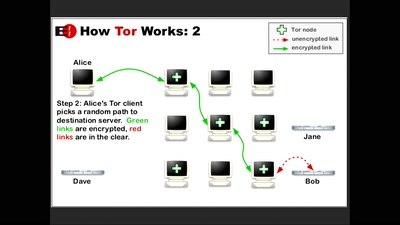
How Alice and Bob meet if they don't like onions
Survey of Network Anonymisation Techniques

58 min
Baseband Exploitation in 2013
Hexagon challenges
46 min
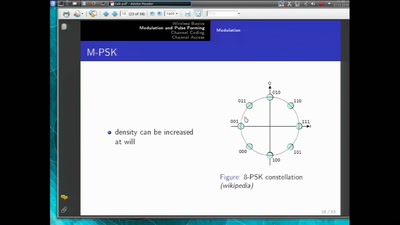
Basics of Digital Wireless Communication
introduction to software radio principles

61 min
An Elevator to the Moon (and back)
Space Transportation and the Extraterrestrial Imperative
62 min