Search for "sECuRE" returned 792 results

40 min
ACE up the sleeve:
Hacking into Apple's new USB-C Controller

59 min
TamaGo - bare metal Go framework for ARM SoCs.
Reducing the attack surface with pure embedded Go.

50 min
How does the Internet work?
An explanation of Inter-Net and everyday protocols

56 min
Planes and Ships and Saving Lives
How soft and hardware can play a key role in saving lives…
34 min
re:claimID
A GNUnet Application for Self-sovereign, Decentralised…

58 min
How to Break PDFs
Breaking PDF Encryption and PDF Signatures

61 min
Uncaging Microchips
Techniques for Chip Preparation
52 min
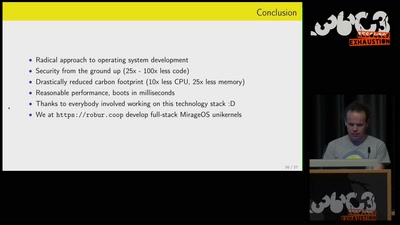
Leaving legacy behind
Reducing carbon footprint of network services with MirageOS…

60 min
Everything you always wanted to know about Certificate Transparency
(but were afraid to ask)
59 min