Search for "W. Heck" returned 1245 results

51 min
Uncovering vulnerabilities in Hoermann BiSecur
An AES encrypted radio system
41 min
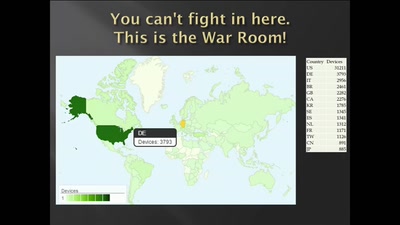
SCADA StrangeLove 2
We already know
61 min
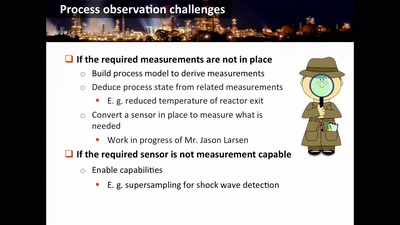
Damn Vulnerable Chemical Process
Exploitation in a new media
60 min
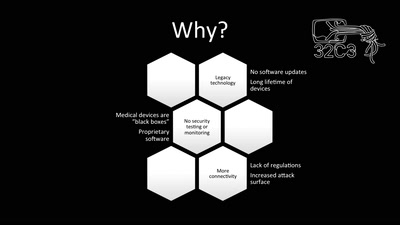
Unpatchable
Living with a vulnerable implanted device

63 min
Traue keinem Scan, den du nicht selbst gefälscht hast
"Bei Kopierern kommt das raus, was man reinsteckt." – Wer…

60 min
Quantum Cryptography
from key distribution to position-based cryptography
38 min
KOALitionsvertragsAnalyse
Mit Tools & Methoden dem Vertrag auf den Zahn fühlen

42 min
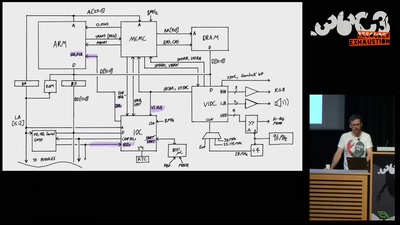
Firmware Fat Camp
Embedded Security Using Binary Autotomy
58 min
The Ultimate Acorn Archimedes talk
Everything about the Archimedes computer (with zero…

34 min
Social Cooling - big data’s unintended side effect
How the reputation economy is creating data-driven…

61 min