Search for "sECuRE" returned 792 results

54 min
Kernel Tracing With eBPF
Unlocking God Mode on Linux

60 min
Shopshifting
The potential for payment system abuse
59 min
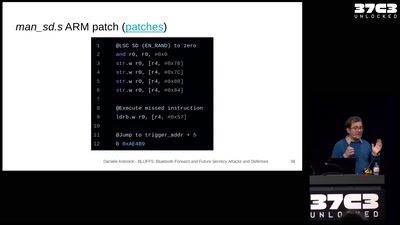
BLUFFS: Bluetooth Forward and Future Secrecy Attacks and Defenses
Breaking and fixing the Bluetooth standard. One More Time.
40 min
Live, Die, Repeat
The fight against data retention and boundless access to…

58 min
Self-encrypting deception
weaknesses in the encryption of solid state drives (SSDs)
61 min
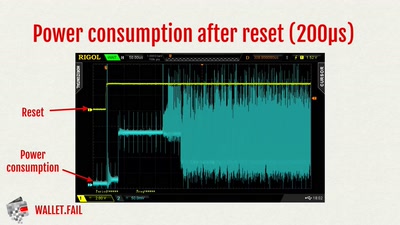
wallet.fail
Hacking the most popular cryptocurrency hardware wallets

55 min
Fuzzing the phone in the iPhone
D-d-d-di-di-d-d-di-d-di-d-di-d-dimm!

56 min
WarGames in memory
what is the winning move?
46 min
What The Fax?!
Hacking your network likes it's 1980 again

58 min
Skynet Starter Kit
From Embodied AI Jailbreak to Remote Takeover of Humanoid…

61 min
Vacuum robot security and privacy
prevent your robot from sucking your data

29 min
What de.fac2?
Attacking an opensource U2F device in 30 minutes or less
40 min