Search for "wsa" returned 5281 results

60 min
Beyond your cable modem
How not to do DOCSIS networks

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

60 min
Quantum Cryptography
from key distribution to position-based cryptography

34 min
Haft für Whistleblower?
Demokratiefeindliches Strafrecht: Die Datenhehlerei gem. §…

64 min
"Exploit" in theater
post-existentialism is the question, not post-privacy
56 min
Iridium Update
more than just pagers
42 min
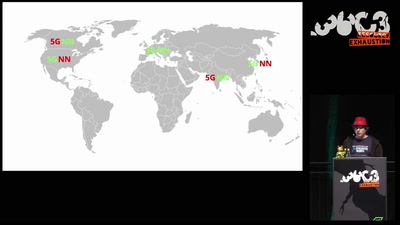
5G & Net Neutrality
Status of the Net Neutrality Reform in Europe

60 min
APT Reports and OPSEC Evolution, or: These are not the APT reports you are looking for
How advanced threat actors learn and change with innovation…
31 min
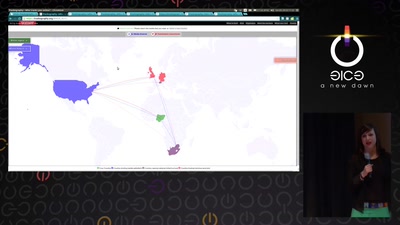
Trackography
You never read alone

56 min
Planes and Ships and Saving Lives
How soft and hardware can play a key role in saving lives…

43 min
#NoPNR – Let’s kill the next Data Retention Law
How to Stop the Dubious Use of Passenger Name Records by…
60 min
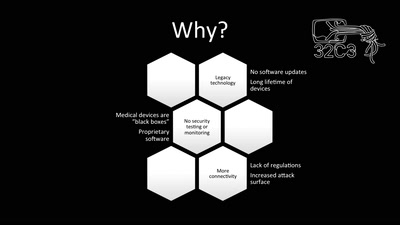
Unpatchable
Living with a vulnerable implanted device
39 min
The Eye on the Nile
Egypt's Civil Society Under Attack
60 min
Inside the Fake Like Factories
How thousands of Facebook, You Tube and Instagram pages…

43 min
Speaking Fiction To Power
Strategies and tactics to ‘hack’ public spaces and social…

43 min