Search for "Jim" returned 4890 results
60 min
Wind: Off-Grid Services for Everyday People
Integrating nearby and offline connectivity with the…

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

59 min
Hacking EU funding for a decentralizing FOSS project
Understanding and adapting EU legal guidelines from a FOSS…

60 min
The Only Thing We Know About Cyberspace Is That Its 640x480
One Terabyte of Kilobyte Age

62 min
The Internet (Doesn't) Need Another Security Guide
Creating Internet Privacy and Security Resources That Don't…

49 min
Toward a Cognitive "Quantified Self"
Activity Recognition for the Mind
31 min
Lightning Talks II
DeepVGI - Einsatz von Lowcost-Lidarsystemen für die…
37 min
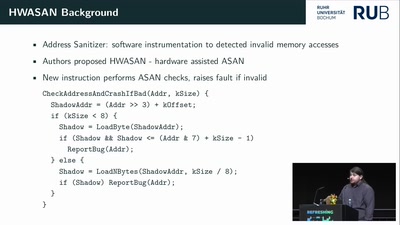
Inside the AMD Microcode ROM
(Ab)Using AMD Microcode for fun and security

32 min
Fuck Dutch mass-surveillance: let's have a referendum!
Forcing the Netherlands to publicly debate privacy and the…

30 min
Syrian Archive
Preserving documentation of human rights violations

39 min
The automobile as massive data gathering source and the consequences for individual…
The next big privacy heist

44 min
ASLR on the line
Practical cache attacks on the MMU
21 min
Designing PCBs with code
Is designing circuits with code instead of CAD the future…
42 min
Hacking the Nintendo Game & Watch
Your princess is AES encrypted in another castle
25 min
Keys of Fury
Type In Beyond the Scrolling Horizon

61 min
Trustworthy secure modular operating system engineering
fun(ctional) operating system and security protocol…

58 min