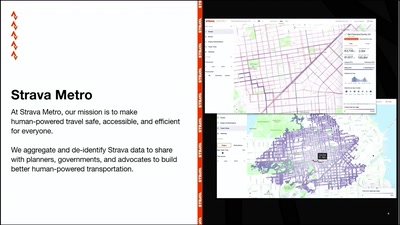
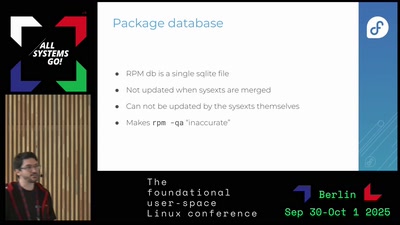
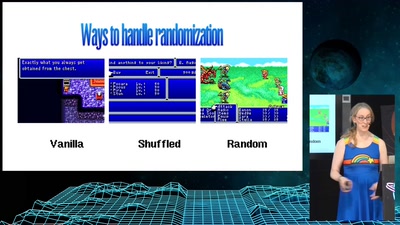
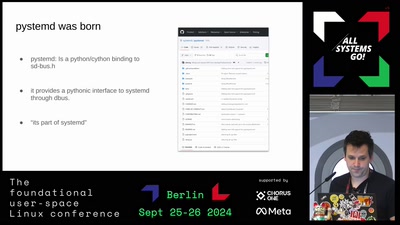
Search for "ICAN" returned 3817 results

44 min
Port Scanning improved
New ideas for old practices

59 min
De-anonymizing Programmers
Large Scale Authorship Attribution from Executable Binaries…
69 min
Implementing flexible page layouts with Drupal
Using the PHPTemplate engine and the Content Construction…
64 min