Search for "LAC team" returned 769 results
62 min
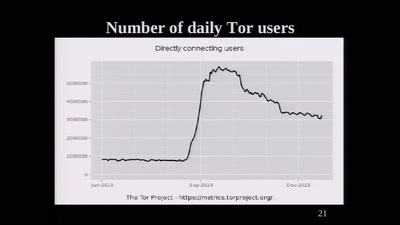
The Tor Network
We're living in interesting times

60 min
On Digitalisation, Sustainability & Climate Justice
A critical talk about sustainability, technology, society,…
41 min
Demoscene now and then
The demoscene is an underground computer art culture.
45 min
HbbTV Security
OMG - my Smart TV got pr0wn3d

113 min
Methodisch inkorrekt!
Die Wissenschaftsgala vom 33C3
59 min
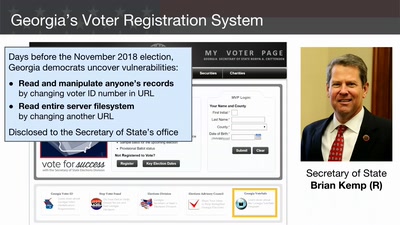
Election Cybersecurity Progress Report
Will the U.S. be ready for 2020?

55 min
Inside Field Station Berlin Teufelsberg
The story of the NSA listening post – told by an ex-SIGINT…

55 min
Fuzzing the phone in the iPhone
D-d-d-di-di-d-d-di-d-di-d-di-d-dimm!

63 min
The Cloud Conspiracy 2008-2014
how the EU was hypnotised that the NSA did not exist

46 min
SELECT code_execution FROM * USING SQLite;
--Gaining code execution using a malicious SQLite database

35 min
Harry Potter and the Not-So-Smart Proxy War
Taking a look at a covert CIA virtual fencing solution

58 min
When hardware must „just work“
An inside look at x86 CPU design
59 min
Where in the World Is Carmen Sandiego?
Becoming a secret travel agent

49 min
C2X: The television will not be revolutionized.
From Cyberfeminism to XenoFeminism

60 min
Attacking end-to-end email encryption
Efail, other attacks and lessons learned.
60 min
Prediction and Control
Watching Algorithms

33 min
Antipatterns und Missverständnisse in der Softwareentwicklung
Eine Geschichte voller Missverständnisse

30 min
Syrian Archive
Preserving documentation of human rights violations
42 min