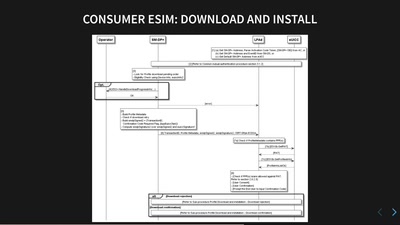
Search for "sECuRE" returned 792 results

29 min
What de.fac2?
Attacking an opensource U2F device in 30 minutes or less

60 min
The rise and fall of Internet voting in Norway
Evaluating a complex cryptographic implementation

33 min
Rebel Cities
Towards A Global Network Of Neighbourhoods And Cities…

53 min
Million Dollar Dissidents and the Rest of Us
Uncovering Nation-State Mobile Espionage in the Wild

60 min
Why is GPG "damn near unusable"?
An overview of usable security research

48 min
Don't Ruck Us Too Hard - Owning Ruckus AP Devices
3 different RCE vulnerabilities on Ruckus Wireless access…

38 min
What your phone won’t tell you
Uncovering fake base stations on iOS devices
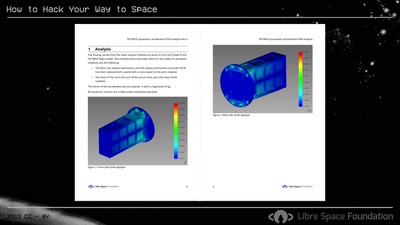
61 min
How to Hack Your Way to Space
Bringing the Hacker Mindset to the Space Ecosphere - The…
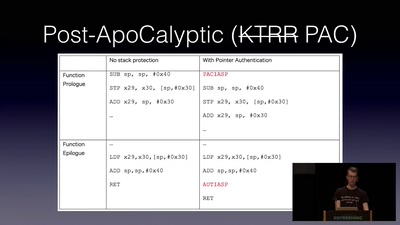
47 min
Jailbreaking iOS
From past to present

61 min