Search for "Jim" returned 4890 results

32 min
Visceral Systems
Approaches to working with sound and network data…

30 min
All Our Shared Spectrum Are Belong to Us
Visualizing WLAN Channel Usage on OpenWRT

38 min
Content take-downs: Who cleans the internet?
EU plans to swipe our freedom of expression under the carpet
60 min
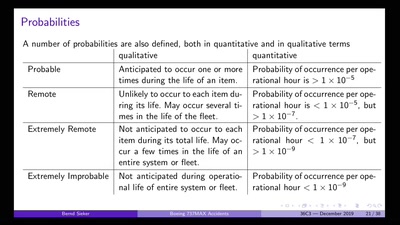
Boeing 737MAX: Automated Crashes
Underestimating the dangers of designing a protection system
42 min
Wifibroadcast
How to convert standard wifi dongles into digital broadcast…

37 min
The foodsaving grassroots movement
How cooperative online structures can facilitate…

55 min
What could possibly go wrong with <insert x86 instruction here>?
Side effects include side-channel attacks and bypassing…
39 min
Why do we need an open food information platform
We want all data about food to be linked and public

58 min
Switches Get Stitches
Industrial System Ownership

32 min
Verified Firewall Ruleset Verification
Math, Functional Programming, Theorem Proving, and an…

30 min
In Search of Evidence-Based IT-Security
IT security is largely a science-free field. This needs to…

30 min
Information Control and Strategic Violence
How governments use censorship and surveillance as part of…

30 min
apertus° AXIOM
The first Open Source Cinema Camera

30 min
Rowhammer.js: Root privileges for web apps?
A tale of fault attacks on DRAM and attacks on CPU caches

37 min
Hacking (with) a TPM
Don't ask what you can do for TPMs, Ask what TPMs can do…

60 min
Open Source is Insufficient to Solve Trust Problems in Hardware
How Betrusted Aims to Close the Hardware TOCTOU Gap
61 min
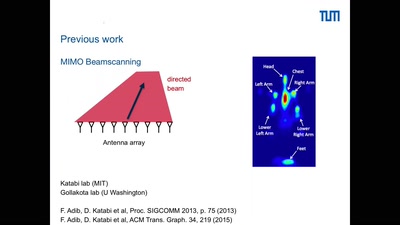
Holography of Wi-Fi radiation
Can we see the stray radiation of wireless devices? And…

55 min