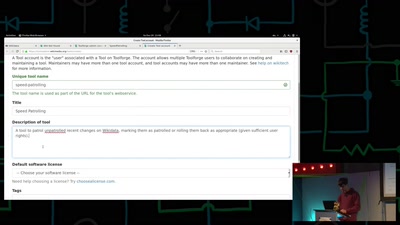
Search for "M" returned 11765 results
60 min
Build your own NSA
How private companies leak your personal data into the…

66 min
Keine Anhaltspunkte für flächendeckende Überwachung
Die Diskussion um NSA, PRISM, Tempora sprachlich und…

60 min
Are machines feminine?
exploring the relations between design and perception of…

51 min
Uncovering vulnerabilities in Hoermann BiSecur
An AES encrypted radio system

49 min
Toward a Cognitive "Quantified Self"
Activity Recognition for the Mind

58 min
Self-encrypting deception
weaknesses in the encryption of solid state drives (SSDs)
58 min
RFID Treehouse of Horror
Hacking City-Wide Access Control Systems

37 min
Hacking (with) a TPM
Don't ask what you can do for TPMs, Ask what TPMs can do…
58 min