Search for "Ezi"
prev
next

60 min
...or why adding BTLE to a device sometimes isn't smart at…

32 min
Automatic detection of key-reuse vulnerabilities

44 min
teaching a new dog old tricks

53 min
An introduction without maths

29 min
Technical Teardown of the Pegasus malware and Trident…

44 min
Tech unexeptionalism and the monopolization of every…

60 min
Offene Boot Firmware leicht gemacht

40 min
Techniques - Tools - Tricks
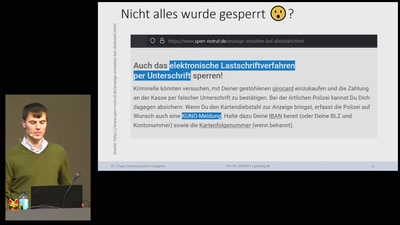
54 min
Über „Girodays“ & anderen Kuriositäten
prev
next



