Search for "Neele" returned 107 results
41 min
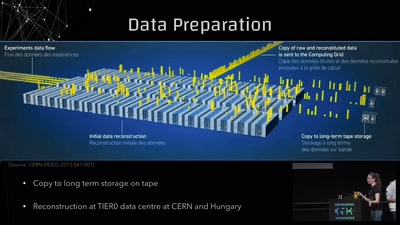
Conquering Large Numbers at the LHC
From 1 000 000 000 000 000 to 10: Breaking down 14 Orders…

101 min
Chaos Communication Slam
Technische Liebesgedichte & Horrorgeschichten im…

38 min
Kickstart the Chaos: Hackerspace gründen für Anfänger
Ein Erfahrungsbericht aus unbetreuter Vereinsmeierei
62 min
Cryptocurrency Hardware Wallets
Building the First Monero Hardware Wallet
61 min
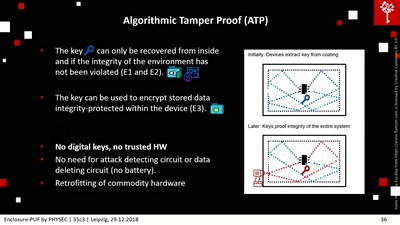
Enclosure-PUF
Tamper Proofing Commodity Hardware and other Applications

61 min
Net Neutrality in Europe
alea iacta est

51 min
Smart Home - Smart Hack
Wie der Weg ins digitale Zuhause zum Spaziergang wird

59 min
Security of the IC Backside
The future of IC analysis

56 min
Reality Check! Basel/Lagos?? In virtual reality?
An African tale of art, culture and technology

60 min
Buffering sucks!
An attempt of calculating the economic cost of buffering.
54 min
Der Kampf um Netzneutralität
Wer kontrolliert das Netz?

61 min