Search for "ar3itrary" returned 246 results
42 min
Wifibroadcast
How to convert standard wifi dongles into digital broadcast…

30 min
Shut Up and Take My Money!
The Red Pill of N26 Security

62 min
Post Memory Corruption Memory Analysis
Automating exploitation of invalid memory writes

50 min
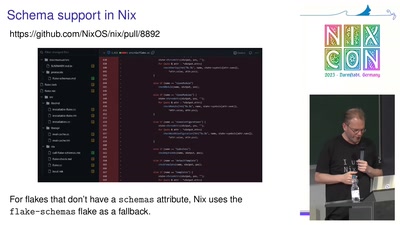
Modern Software Packaging for Developers
Wait, how to install your FOSS project again?
63 min
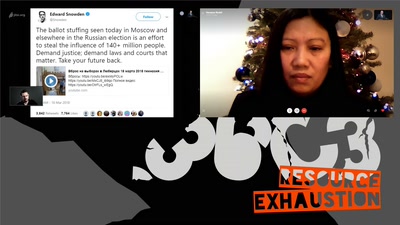
Human Rights at a Global Crossroads
Whistleblowers and the Cases of The Snowden Refugees and…

48 min
Don't Ruck Us Too Hard - Owning Ruckus AP Devices
3 different RCE vulnerabilities on Ruckus Wireless access…

41 min
MicroPython – Python for Microcontrollers
How high-level scripting languages make your hardware…

41 min
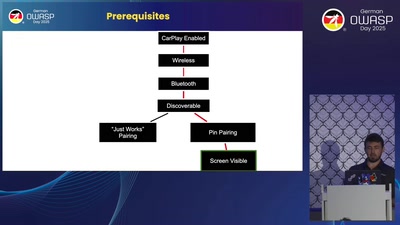
Back in the Driver's Seat
Recovering Critical Data from Tesla Autopilot Using Voltage…
61 min