Search for "monic" returned 66 results

61 min
Deploying TLS 1.3: the great, the good and the bad
Improving the encrypted the web, one round-trip at a time
31 min
Media Disruption Led By The Blind
Hacking Visual Culture
37 min
Listening Back Browser Add-On Tranlates Cookies Into Sound
The Sound of Surveillance

62 min
Kyber and Post-Quantum Crypto
How does it work?

60 min
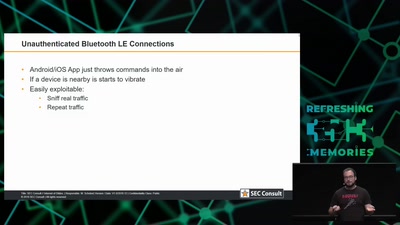
Lockpicking in the IoT
...or why adding BTLE to a device sometimes isn't smart at…
32 min
Internet of Dongs
A long way to a vibrant future
56 min
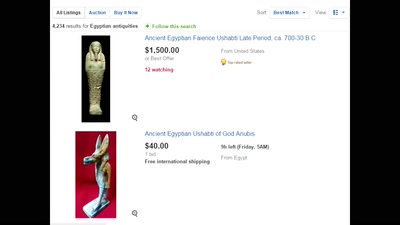
The mummy unwrapped
Cultural Commons durch Kunstraub

46 min
SELECT code_execution FROM * USING SQLite;
--Gaining code execution using a malicious SQLite database

63 min
All cops are broadcasting
TETRA unlocked after decades in the shadows
22 min
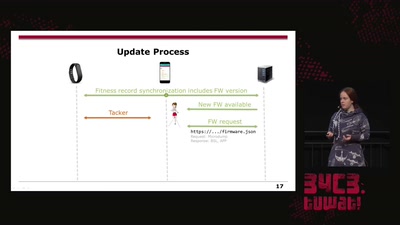
Doping your Fitbit
On Fitbit Firmware Modifications and Data Extraction

63 min
Synthetic Sentience
Can Artificial Intelligence become conscious?

32 min
The Case for Scale in Cyber Security
Security Track Keynote

61 min
About Gamma-Ray Bursts And Boats
What We (Don't) Know About the Most Energetic Events in the…
47 min
Going Deep Underground to Watch the Stars
Neutrino Astronomy with Hyper-Kamiokande

36 min