Search for "wonko" returned 39 results

63 min
All cops are broadcasting
TETRA unlocked after decades in the shadows

62 min
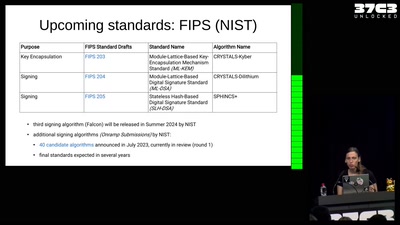
Kyber and Post-Quantum Crypto
How does it work?

61 min
Deploying TLS 1.3: the great, the good and the bad
Improving the encrypted the web, one round-trip at a time

36 min
A Blockchain Picture Book
Blockchain origins and related buzzwords, described in…

63 min
A look into the Mobile Messaging Black Box
A gentle introduction to mobile messaging and subsequent…

64 min
Decoding the LoRa PHY
Dissecting a Modern Wireless Network for the Internet of…

37 min