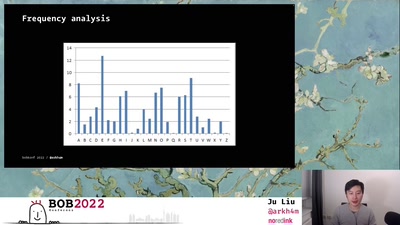
Search for "Inc.)" returned 11273 results

46 min
Introduction to YubiKeys (in openSUSE)
Everything you should know about YubiKey

46 min
Electronic Evicence in Criminal Matters
An introduction and critique of the EC proposal for a…
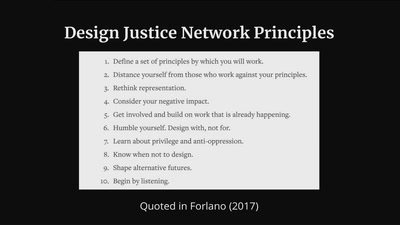
35 min
Wie Freifunken in der Asylindustrie?
Notizen aus der Partizipationsforschung

59 min
Developments in Coordinated Vulnerability Disclosure
The government is here to help

48 min
Lücken in der technischen Selbstverteidigung
Open the Blackbox, Close the Bugdoor

64 min
What is in a name?
Identity-Regimes from 1500 to the 2000s

56 min
Rootkits in your Web application
Achieving a permanent stealthy compromise of user accounts…

52 min