Search for "sECuRE" returned 792 results

55 min
White-Box Cryptography
Survey

53 min
Cryptography demystified
An introduction without maths

51 min
The GNU Name System
A Decentralized PKI For Social Movements
61 min
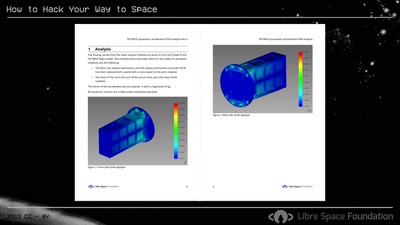
How to Hack Your Way to Space
Bringing the Hacker Mindset to the Space Ecosphere - The…
45 min
SCADA - Gateway to (s)hell
Hacking industrial control gateways

58 min
The Magic World of Searchable Symmetric Encryption
A brief introduction to search over encrypted data

60 min
The plain simple reality of entropy
Or how I learned to stop worrying and love urandom

61 min
Now I sprinkle thee with crypto dust
Internet reengineering session

60 min
Quantum Cryptography
from key distribution to position-based cryptography

35 min
Harry Potter and the Not-So-Smart Proxy War
Taking a look at a covert CIA virtual fencing solution

28 min
Long war tactics
or how we learned to stop worrying and love the NSA

60 min
Check your privileges!
How to drop more of your privileges to reduce attack…

60 min