Search for "Andi Rüther" returned 707 results
38 min
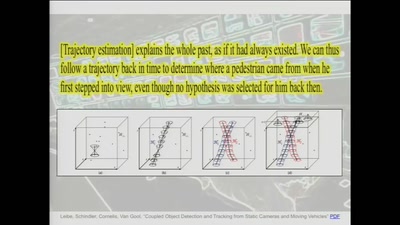
Policing the Romantic Crowd
Velocipedes and Face Recognition
60 min
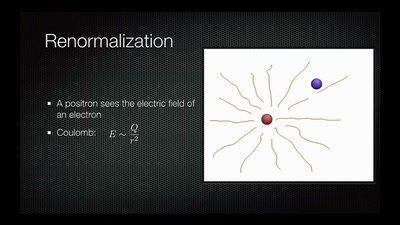
Desperately Seeking Susy
A farewell to a bold proposal?

62 min
Tell no-one
A century of secret deals between the NSA and the telecom…
36 min
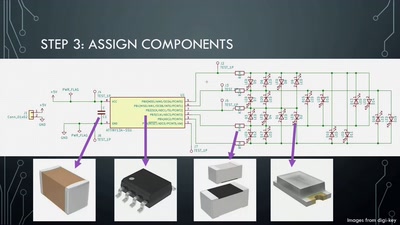
Artistic PCB Design and Fabrication
From doodle to manufacture: how I make mechanically…

60 min
The rise and fall of Internet voting in Norway
Evaluating a complex cryptographic implementation

22 min
Trust us and our business will expand!
Net-activism strategies against fake web companies

57 min
Everything you want to know about x86 microcode, but might have been afraid to ask
An introduction into reverse-engineering x86 microcode and…

44 min
Disclosure DOs, Disclosure DON'Ts
Pragmatic Advice for Security Researchers

48 min
Seidenstraße
The Making of…

53 min
When algorithms fail in our personal lives
Social media break up coordinator

54 min
Attacking Chrome IPC
Reliably finding bugs to escape the Chrome sandbox
31 min
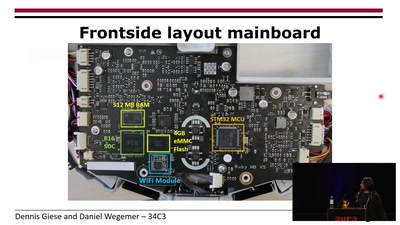
Unleash your smart-home devices: Vacuum Cleaning Robot Hacking
Why is my vacuum as powerful as my smartphone?

53 min
Surveilling the surveillers
About military RF communication surveillance and other…

60 min
Building a high throughput low-latency PCIe based SDR
Lessons learnt implementing PCIe on FPGA for XTRX Software…

30 min