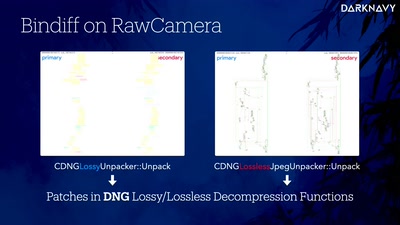
Search for "rem0te" returned 820 results

29 min
What de.fac2?
Attacking an opensource U2F device in 30 minutes or less

46 min
SELECT code_execution FROM * USING SQLite;
--Gaining code execution using a malicious SQLite database
39 min
Decentralized energy production: green future or cybersecurity nightmare?
The cybersecurity dark side of solar energy when clouds are…

40 min
Domain computers have accounts, too!
Owning machines through relaying and delegation

39 min
Configuration Driven Event Tracing with Traceleft and eBPF
Use cases and implementation challenges
36 min
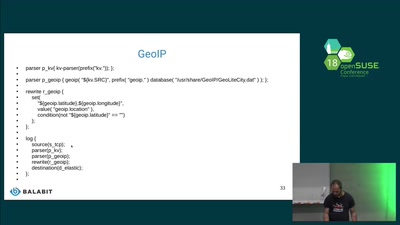
Logging containers
Collecting host, docker and container logs centrally
30 min
Tumbleweed Snapshots: Rolling With You
The missing link between fixed and rolling releases

48 min
Turn off the Stockholm Programme!
Campaign against the next five-years plan for EU homeland…
42 min
Wifibroadcast
How to convert standard wifi dongles into digital broadcast…
59 min
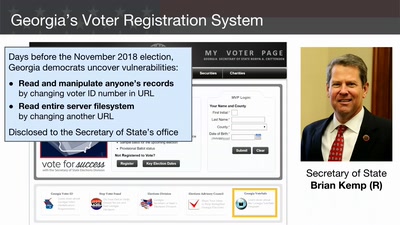
Election Cybersecurity Progress Report
Will the U.S. be ready for 2020?

41 min