Search for "Seth Hardy" returned 899 results

63 min
Dissecting HDMI
Developing open, FPGA-based capture hardware for conference…

49 min
C2X: The television will not be revolutionized.
From Cyberfeminism to XenoFeminism
64 min
Hacking the Media: Geflüchtete schmuggeln, Nazis torten, Pässe fälschen
Warum wir zivilen Ungehorsam und Subversion mehr brauchen…

40 min
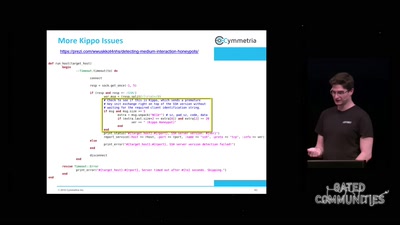
An introduction to Firmware Analysis
Techniques - Tools - Tricks

60 min
From Computation to Consciousness
How computation helps to explain mind, universe and…

60 min
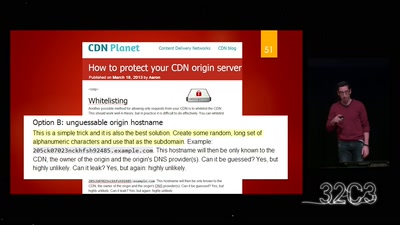
APT Reports and OPSEC Evolution, or: These are not the APT reports you are looking for
How advanced threat actors learn and change with innovation…
41 min
Framing digital industry into planetary limits and transition policies
The environmental costs of digital industry and pathways to…

60 min
The rise and fall of Internet voting in Norway
Evaluating a complex cryptographic implementation

46 min
Writing secure software
using my blog as example

55 min
Graphs, Drones & Phones
The role of social-graphs for Drones in the War on Terror.

59 min
How to teach programming to your loved ones
Enabling students over example-driven teaching
32 min
Coding your body
How to decipher the messages of your body

57 min
A Dozen Years of Shellphish
From DEFCON to the DARPA Cyber Grand Challenge

32 min
Relativitätstheorie für blutige Anfänger
Raum, Zeit, Licht und Gravitation, wie hängt das zusammen?

53 min