Search for "Udo Vetter" returned 1175 results
59 min
The Ultimate SPC700 Talk
The hardware behind the music of Super Mario World, Chrono…

58 min
Self-encrypting deception
weaknesses in the encryption of solid state drives (SSDs)

64 min
Cory Doctorow – Fireside Chat
Reading and Q&A

61 min
About Gamma-Ray Bursts And Boats
What We (Don't) Know About the Most Energetic Events in the…

30 min
apertus° AXIOM
The first Open Source Cinema Camera
41 min
Infrastructure of a migratory bird
Technology and autonomy in more-than-human networks

63 min
Dissecting HDMI
Developing open, FPGA-based capture hardware for conference…
56 min
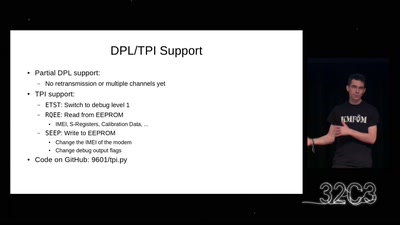
Iridium Update
more than just pagers
39 min
Gamified Control?
China's Social Credit Systems

30 min
In Search of Evidence-Based IT-Security
IT security is largely a science-free field. This needs to…
45 min
SCADA - Gateway to (s)hell
Hacking industrial control gateways
31 min
Nerds in the news
Spending a year coding in a newsroom
39 min

![Why we are addicted to lithium [2/2]](https://static.media.ccc.de/media/events/rc3/2021/194-17816a45-eea7-5b85-b623-5f343aec59de.jpg)