Search for "sECuRE" returned 792 results

43 min
Tractors, Rockets and the Internet in Belarus
How belarusian authoritarian regime is using technologies…

55 min
The DROWN Attack
Breaking TLS using SSLv2

57 min
Everything you want to know about x86 microcode, but might have been afraid to ask
An introduction into reverse-engineering x86 microcode and…
38 min
Unpacking the compromises of Aadhaar, and other digital identities inspired by it
Governments around the world are implementing digital…

31 min
PUFs, protection, privacy, PRNGs
an overview of physically unclonable functions

58 min
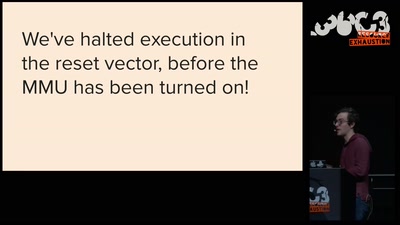
Thwarting Evil Maid Attacks
Physically Unclonable Functions for Hardware Tamper…

40 min
Verlorene Domains, offene Türen
Was alte Behördendomains verraten

58 min
Taming the Chaos: Can we build systems that actually work?
Possible paths from today's ghastly hackery to what…
22 min
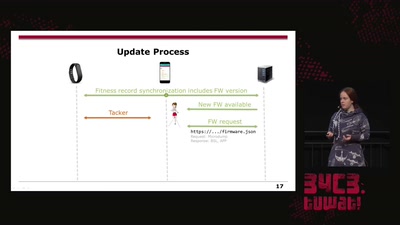
Doping your Fitbit
On Fitbit Firmware Modifications and Data Extraction
62 min