Search for "ALX" returned 5874 results
41 min
Framing digital industry into planetary limits and transition policies
The environmental costs of digital industry and pathways to…

58 min
The Magic World of Searchable Symmetric Encryption
A brief introduction to search over encrypted data

60 min
Attacking end-to-end email encryption
Efail, other attacks and lessons learned.

60 min
Internet Cube
Let's Build together a Free, Neutral and Decentralized…

28 min
Long war tactics
or how we learned to stop worrying and love the NSA

59 min
De-anonymizing Programmers
Large Scale Authorship Attribution from Executable Binaries…

60 min
Why is GPG "damn near unusable"?
An overview of usable security research

60 min
The Fight for Encryption in 2016
Crypto fight in the Wake of Apple v. FBI

60 min
Vor Windows 8 wird gewarnt
Und nichts (Secure) Bootet mehr?

30 min
apertus° AXIOM
The first Open Source Cinema Camera
22 min
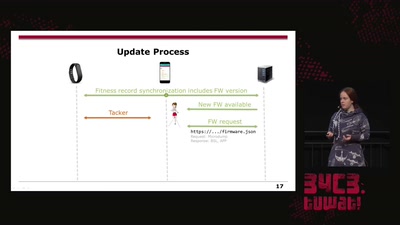
Doping your Fitbit
On Fitbit Firmware Modifications and Data Extraction
61 min
Trügerische Sicherheit
Wie die Überwachung unsere Sicherheit gefährdet

30 min
In Search of Evidence-Based IT-Security
IT security is largely a science-free field. This needs to…

30 min
Rowhammer.js: Root privileges for web apps?
A tale of fault attacks on DRAM and attacks on CPU caches

33 min
Interplanetary Colonization
the state at the beginning of the 21st Century

43 min